
This sponsored article is brought to you by NYU Tandon School of Engineering.
In our digital age, where information flows seamlessly through the vast network of the internet, the importance of encrypted data cannot be overstated. As we share, communicate, and store an increasing amount of sensitive information online, the need to safeguard it from prying eyes and malicious actors becomes paramount. Encryption serves as the digital guardian, placing our data in a lockbox of algorithms that only those with the proper key can unlock.
Whether it’s personal messages, health data, financial transactions, or confidential business communications, encryption plays a pivotal role in maintaining privacy and ensuring the integrity of our digital interactions. Typically, data encryption protects data in transit: it’s locked in an encrypted “container” for transit over potentially unsecured networks, then unlocked at the other end, by the other party for analysis. But outsourcing to a third-party is inherently insecure.

But what if encryption didn’t just exist in transit and sit unprotected on either end of the transmission? What if it was possible to do all of your computer work — from basic apps to complicated algorithms — fully encrypted, from beginning to end.
That is the task being taken up by Brandon Reagen, Assistant Professor of Computer Science and Engineering and Electrical and Computer Engineering at the NYU Tandon School of Engineering. Reagen, who is also a member of the NYU Center for Cybersecurity, focuses his research on designing specialized hardware accelerators for applications including privacy preserving computation. And now, he is proving that the future of computing can be privacy-forward while making huge advances in information processing and hardware design.
All-encompassing Encryption
In a world where cyber threats are ever-evolving and data breaches are a constant concern, encrypted data acts as a shield against unauthorized access, identity theft, and other cybercrimes. It provides individuals, businesses, and organizations with a secure foundation upon which they can build trust and confidence in the digital realm.
The goal of cybersecurity researchers is the protection of your data from all sorts of bad actors — cybercriminals, data-hungry companies, and authoritarian governments. And Reagen believes encrypted computing could hold an answer. “This sort of encryption can give you three major things: improved security, complete confidentiality and sometimes control over how your data is used,” says Reagen. “It’s a totally new level of privacy.”
“My aim is to develop ways to run expensive applications, for example, massive neural networks, cost-effectively and efficiently, anywhere, from massive servers to smartphones” —Brandon Reagen, NYU Tandon
Fully homomorphic encryption (FHE), one type of privacy preserving computation, offers a solution to this challenge. FHE enables computation on encrypted data, or ciphertext, to keep data protected at all times. The benefits of FHE are significant, from enabling the use of untrusted networks to enhancing data privacy. FHE is an advanced cryptographic technique, widely considered the “holy grail of encryption,” that enables users to process encrypted data while the data or models remain encrypted, preserving data privacy throughout the data computation process, not just during transit.
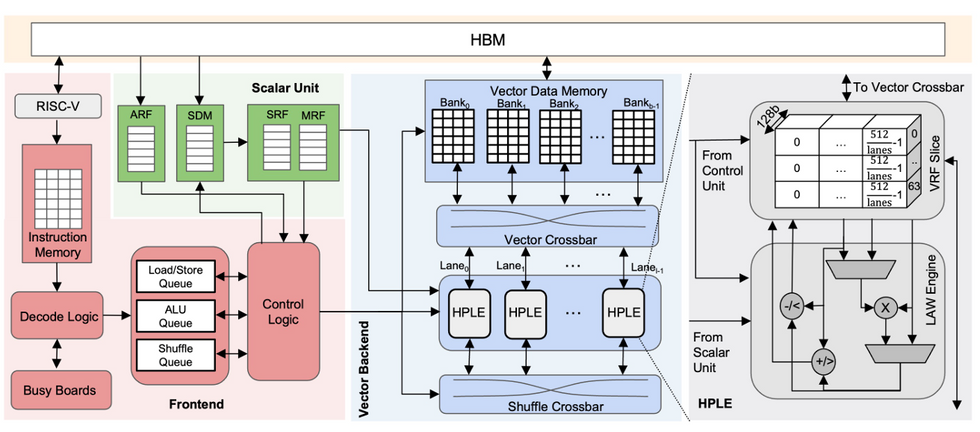
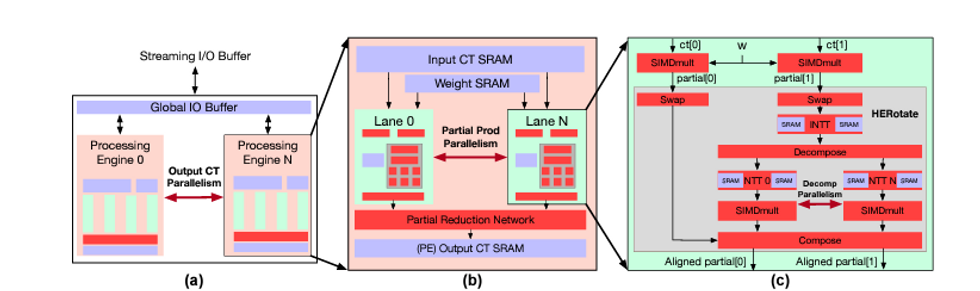
While a number of FHE solutions have been developed, running FHE in software on standard processing hardware remains untenable for practical data security applications due to the massive processing overhead. Reagen and his colleagues have recently been working on a DARPA-funded project called The Data Protection in Virtual Environments (DPRIVE) program, that seeks to speed up FHE computation to more usable levels.
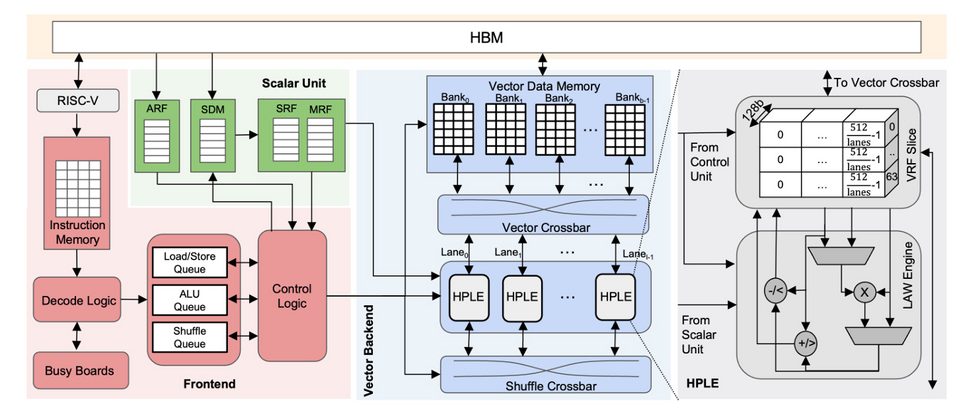
Specifically, the program seeks to develop novel approaches to data movement and management, parallel processing, custom functional units, compiler technology, and formal verification methods that ensure the design of the FHE implementation is effective and accurate, while also dramatically decreasing the performance penalty incurred by FHE computations. The target accelerator should reduce the computational run time overhead by many orders of magnitude compared to current software-based FHE computations on conventional CPUs, and accelerate FHE calculations to within one order of magnitude of current performance on unencrypted data.
The Hardware Promising Privacy
While FHE has been shown to be possible, the hardware required for it to be practical is still rapidly being developed by researchers. Reagen and his team are designing it from the ground up, including new chips, datapaths, memory hierarchies, and software stacks to make it all work together.
The team was the first to show that the extreme levels of speedup needed to make HE feasible was possible. And by early next year, they’ll begin manufacturing of their prototypes to further their field testing.
Reagen — who earned a doctoral degree in computer science from Harvard in 2018 and undergraduate degrees in computer systems engineering and applied mathematics from the University of Massachusetts, Amherst, in 2012 — focused on creating specialized hardware accelerators for applications like deep learning. These accelerators enhance specialized hardware that can be made orders of magnitude more efficient than general-purpose platforms like CPUs. Enabling accelerators requires changes to the entire compute stack, and to bring about this change, he has made several contributions to lowering the barrier of using accelerators as general architectural constructs, including benchmarking, simulation infrastructure, and System on a Chip (SoC) design.
“My aim is to develop ways to run expensive applications, for example, massive neural networks, cost-effectively and efficiently, anywhere, from massive servers to smartphones,” he says.
Before coming to NYU Tandon, Reagen was a former research scientist on Facebook’s AI Infrastructure Research team, where he became deeply involved in studying privacy. This combination of a deep cutting-edge computer hardware background and a commitment to digital security made him a perfect fit for NYU Tandon and the NYU Center for Cybersecurity, which has been at the forefront of cybersecurity research since its inception.
“A lot of the big problems that we have in the world right now revolve around data. Consider global health coming off of COVID: if we had better ways of computing global health data analytics and sharing information without exposing private data, we might have been able to respond to the crisis more effectively and sooner” —Brandon Reagen, NYU Tandon
For Reagen, this is an exciting moment in the history of privacy preserving computation, a field that will have huge implications for the future of data and computing.
“I’m an optimist — I think this could have as big an impact as the Internet itself,” says Reagen. “And the reason is that, if you think about a lot of the big problems that we have in the world right now, a lot of them revolve around data. Consider global health. We’re just coming off of COVID, and if we had better ways of computing global health data analytics and sharing information without exposing private data, we might have been able to respond to the crisis more effectively and sooner. If we had better ways of sharing data about climate change data from all over the world, without exposing what each individual country or state or city was actually emitting, you could imagine better ways of managing and fighting global climate change. These problems are, in large part, problems of data, and this kind of software can help us solve them.”
Reference: https://ift.tt/GjJRe7O
No comments:
Post a Comment