

Enlarge (credit: Getty Images)
Exploit code for a critical printer software vulnerability became publicly available on Monday in a release that may exacerbate the threat of malware attacks that have already been underway for the past five days.
The vulnerability resides in print management software known as PaperCut, which the company’s website says has more than 100 million users from 70,000 organizations. When this post went live, the Shodan search engine showed that close to 1,700 instances of the software were exposed to the Internet.
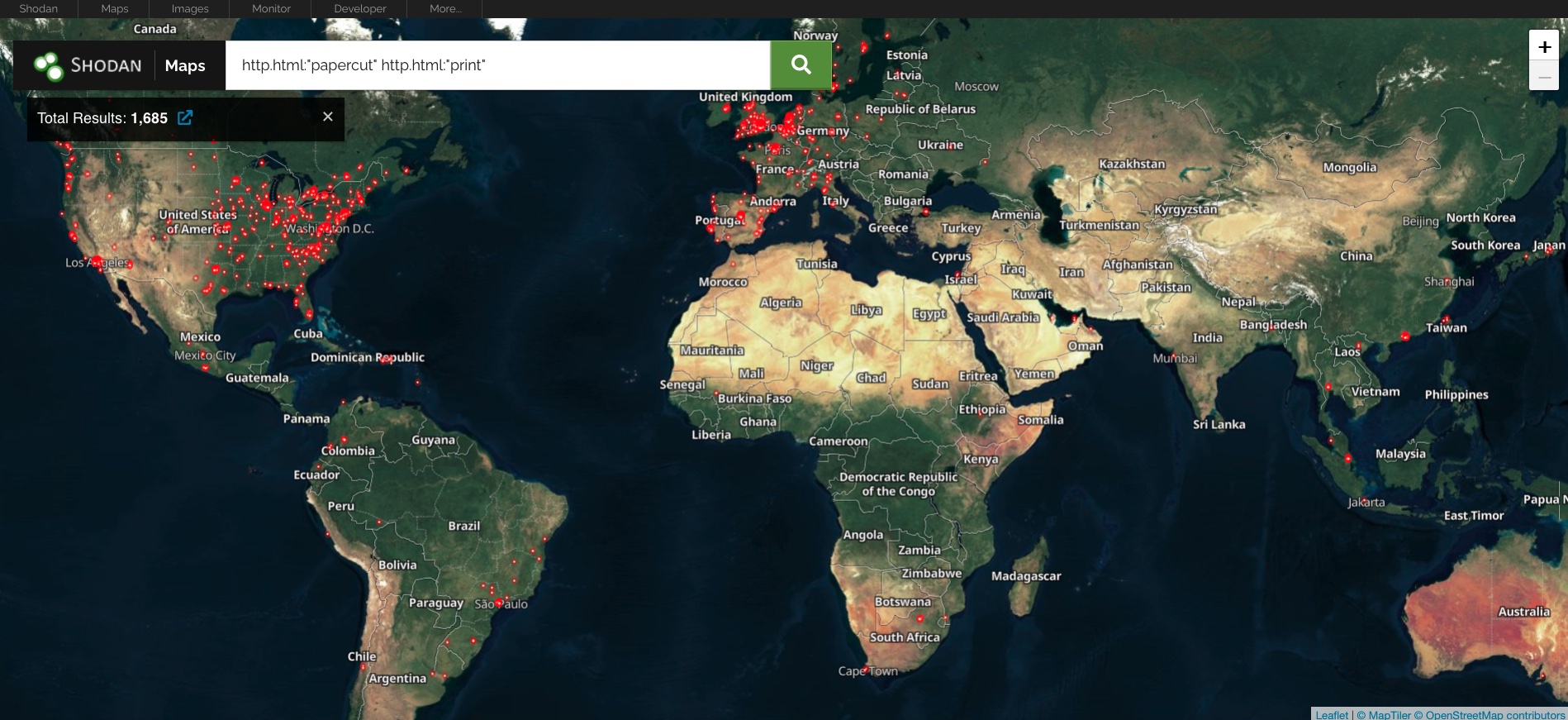
World map showing locations of PaperCut installations.
Last Wednesday, PaperCut warned that a critical vulnerability it patched in the software in March was under active attack against machines that had yet to install the March update. The vulnerability, tracked as CVE-2023–27350, carries a severity rating of 9.8 out of a possible 10. It allows an unauthenticated attacker to remotely execute malicious code without needing to log in or provide a password. A related vulnerability, tracked as CVE-2023–27351 with a severity rating of 8.2, allows unauthenticated attackers to extract usernames, full names, email addresses, and other potentially sensitive data from unpatched servers.

No comments:
Post a Comment