

Enlarge (credit: Peach_istock via Getty Images)
It is common to hear news reports about large data breaches, but what happens once your personal data is stolen? Our research shows that, like most legal commodities, stolen data products flow through a supply chain consisting of producers, wholesalers, and consumers. But this supply chain involves the interconnection of multiple criminal organizations operating in illicit underground marketplaces.
The stolen data supply chain begins with producers—hackers who exploit vulnerable systems and steal sensitive information such as credit card numbers, bank account information, and Social Security numbers. Next, the stolen data is advertised by wholesalers and distributors who sell the data. Finally, the data is purchased by consumers who use it to commit various forms of fraud, including fraudulent credit card transactions, identity theft, and phishing attacks.
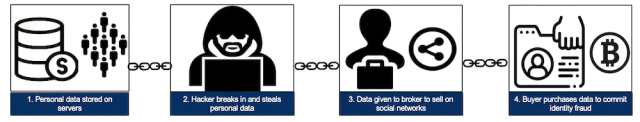
The stolen data supply chain, from data theft to fraud. (credit: Christian Jordan Howell (CC BY ND))
This trafficking of stolen data between producers, wholesalers, and consumers is enabled by darknet markets, which are websites that resemble ordinary e-commerce websites but are accessible only using special browsers or authorization codes.

No comments:
Post a Comment